An era of unprecedented connectivity and convenience has arrived with the advent of the Internet of Things (IoT). IoT has the potential to revolutionize industries and improve our daily lives through smart homes and industrial automation. But this intricate ecosystem also poses significant cybersecurity difficulties. The vulnerabilities created by billions of devices joining a vast network open doors for cyberattacks. Data security in the IoT landscape must be balanced with the protection of vital infrastructure, individual privacy, and even national security.
Recognizing the IoT Environment
The network of interconnected objects known as the “Internet of Things” uses the Internet to communicate and exchange data without the need for human intervention. These gadgets can be anything from commonplace items like wearable fitness trackers and smart thermostats to commercial machinery, medical equipment, and even autonomous vehicles. With devices used in a variety of industries and use cases, the IoT ecosystem is distinguished by its diversity.
The ability of the IoT to gather, examine, and take action on enormous amounts of data is what gives it its transformative potential. This information can boost productivity, enable preventive maintenance, and produce customized experiences. But the connectivity that gives the IoT its power also leaves it open to cybersecurity risks.
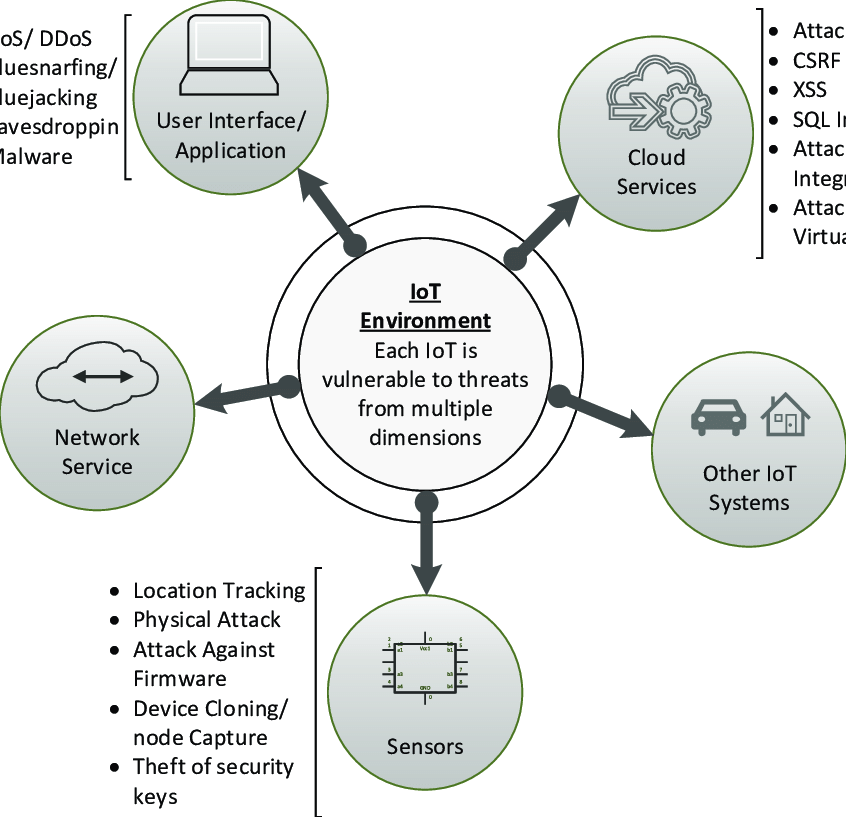
The evolving threat environment: Keep Informed
Following are some significant advancements and details that all IoT users need to be aware of:
- Increased Vulnerabilities: As IoT devices quickly proliferate, the attack surface for cybercriminals is growing. Recent reports have uncovered flaws in a number of IoT devices, potentially endangering user privacy and data security. IoT users must stay informed about these vulnerabilities and take appropriate action to reduce the risks that come with them.
- Privacy issues with data: IoT devices produce enormous amounts of data, often including sensitive and personal data. It is critical for users to comprehend how IoT devices and related services collect, store, and use their data. The best ways to protect personal information include reading privacy policies, exercising caution when granting permissions, and taking into account data protection features.
- Supply Chain Security: Potential security risks are introduced by the intricate supply chain used in the production of IoT devices. Recent occurrences have made it known that compromised devices have been sold to unwary customers. To prevent potential security breaches, it’s crucial to buy IoT devices from reputable manufacturers and merchants and to confirm their authenticity and integrity.
- Regulatory Actions: Governments and regulatory bodies are taking action to address the risks associated with IoT security as they recognize its importance. Users should keep up with the most recent rules and recommendations for IoT security in their respective countries. These regulations’ observance can guarantee greater security for IoT devices and safeguard user privacy.
- Threats from botnets: Botnets are networks of compromised devices that hackers control. Large-scale distributed denial-of-service (DDoS) attacks can be launched using them, along with other nefarious tasks. Recent occurrences have shown that vulnerable IoT devices could be the target of botnets. To reduce the chance of being enlisted into a botnet, users should make sure that their IoT devices are secured with strong passwords, frequently updated firmware, and secure communication protocols.
- Failure to Encrypt: For the protection of IoT communications and the data sent between devices and cloud platforms, encryption is essential. Sensitive information can be intercepted and altered without the proper encryption protocols. In IoT environments, it’s critical to use powerful encryption algorithms and secure communication channels to protect data privacy and integrity.
IoT Security Incidents in the Real World
Numerous high-profile incidents have brought attention to the IoT ecosystem’s vulnerabilities and underlined the urgent need for effective cybersecurity measures:
- (2010) Stuxnet: Stuxnet demonstrated the potential repercussions of a cyberattack on industrial control systems, despite not being a typical IoT incident. The worm specifically targeted Iran’s nuclear facilities and used its control systems to physically harm centrifuges. The dangers of insecure industrial IoT deployments were highlighted by this incident.
- Jeep Cherokee Hack (2015): Security experts demonstrated a flaw that gave them the ability to remotely control the steering, brakes, and transmission of a Jeep Cherokee. This incident brought to light the potential risks posed by unreliable IoT systems in the automotive sector.
- 2016 Mirai Botnet Attack: Insecure IoT device flaws were taken advantage of by the Mirai botnet attack to launch DDoS attacks against a variety of targets. Major websites and online services were disrupted by the attack, which highlighted the potential consequences of unsecured IoT devices being used for nefarious ends.
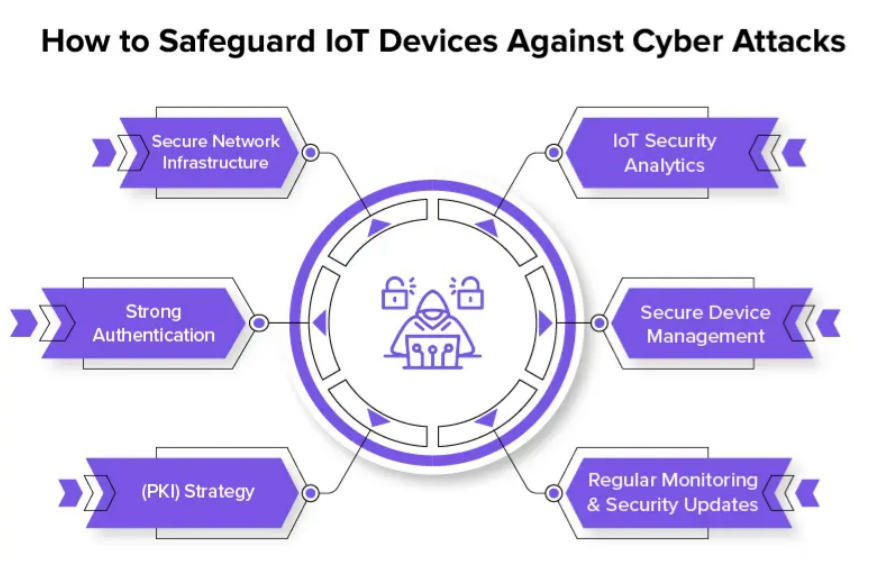
How to Prevent Cyberattacks on IoT Devices
IoT security issues were not addressed until major hacking attacks like Stuxnet, Brickerbot, Mirai, and Abbot exposed vulnerabilities. Businesses must prioritize proactive cybersecurity measures to secure IoT connections and prevent data breaches. Best practices include:
- Network Security Infrastructure: The network that serves as a link between IoT devices and back-end systems must be secured at all costs. This can be done by putting security tools like firewalls, intrusion detection, antivirus, anti-malware, VPNs, and prevention systems in place. In order to maintain a smooth operation, the network must be effectively protected against unauthorized access and malicious attacks using the systems mentioned above.
- Effective Authentication: IoT cybersecurity solutions include strong authentication features for connected devices, such as multi-factor authentication, digital certificates, and biometric systems. These measures protect devices from external security breaches, ensuring data security and reducing the risk of data loss. This benefits connected devices at home, office, and anywhere.
- Security Analytics for IoT: By using security analytics, you can significantly reduce the number of security issues you encounter. This calls for gathering, comparing, and analyzing data from various sources, and it can aid IoT security providers in identifying potential threats.
- Managed Device Security: To efficiently identify potential threats and address security incidents, companies should implement best practices for secure device management, such as strong password strategies, remote device monitoring, and centralized control. Use different passwords for every device, and think about changing them frequently. Useless passwords like “your name,” “date of birth,” or “123456” should be avoided.
- Updates to Security and Regular Monitoring: Businesses must adopt a proactive strategy, including constant monitoring and routine updates, to ensure secure IoT connections and reduce malicious attacks by detecting unusual activities and vulnerabilities.
Innovations in IoT Security
As the difficulties in securing IoT increase, new technological developments are emerging to solve these problems:
- Using blockchain to secure IoT: The decentralized and immutable characteristics of blockchain can increase the security of IoT transactions and data transfers. Within the ecosystem, it can foster transparency and trust.
- Threat Detection Driven by AI: IoT device data is generated in large quantities, which AI algorithms can analyze to find patterns indicating potential cyber threats. Intrusion detection systems powered by AI can deliver alerts and responses in real time.
- Using the Edge: Edge computing reduces the amount of data transmitted over networks by processing data closer to the source. By doing so, the attack surface can be reduced, and the risks posed by cloud-based attacks can be lessened.
- HSMs, or Hardware Security Modules: HSMs offer hardware that is impervious to tampering for cryptographic operations. They can be incorporated into IoT devices to strengthen encryption and safeguard private information.
The value of cybersecurity cannot be overstated as the IoT landscape develops. Because IoT devices are interconnected, a security breach in one device could potentially compromise an entire network. A proactive, multifaceted strategy that integrates technology, policy, education, and collaboration is needed to secure the IoT ecosystem.
In the end, it’s essential to strike a balance between utilizing the IoT’s transformative potential and reducing its inherent risks. Technology is advancing, and with it must come a greater understanding of the cybersecurity issues it poses. We can create a more secure and resilient IoT ecosystem that enables us to fully enjoy the advantages of the connected world by encouraging a culture of security awareness and innovation.