When two processes are running in the same host, the Operating System of the host facilitates the communication. The processes can communicate with each other via inter-process communication governed by the OS. But our objective of this tutorial, and this course, is not how processes on the same host communicate. We are interested in how processes on different hosts (with potentially different operating systems) communicate over the network.
To exchange information and coordinate their activities the network applications must communicate with each other. Network applications typically involve multiple processes running on different devices that need to communicate with each other in order to function properly.
Below is a list of Common IPC mechanisms used in Network Application.
Common IPC mechanisms used in Network Application
Common IPC mechanisms used in this context include:
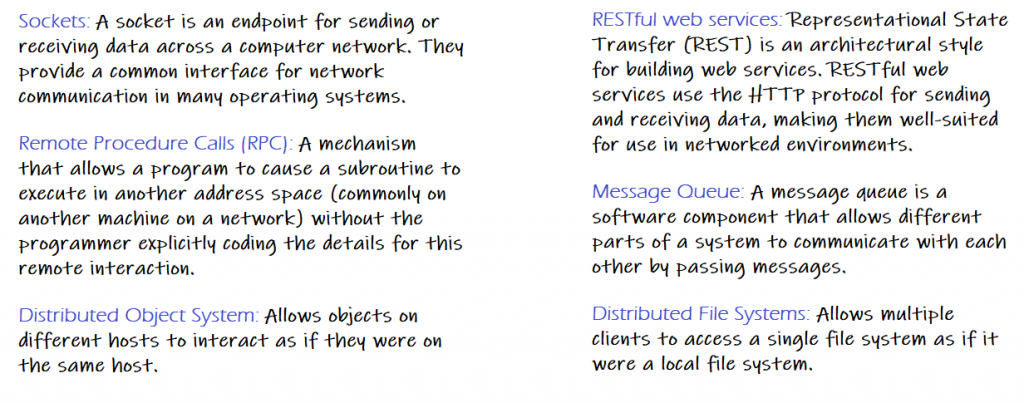
These are some of the common IPC mechanisms used in networked environments, each with their own strengths and weaknesses depending on the specific use case and requirements of the application.
Inter-process communication (IPC) is needed in network applications because it allows different processes running on different devices to exchange information and coordinate their activities. Network applications typically involve multiple processes running on different devices that need to communicate with each other in order to function properly.
Take your coding skills to the next level with our comprehensive guides, “Python Beginner to Advanced” and “Java Beginner to Advanced.” Whether you’re diving into Python or mastering Java, these books provide step-by-step guidance and in-depth knowledge to elevate your programming expertise.
Importance of Inter-process Communication
Some of the reasons why IPC is needed in network applications include:

To put it simply, IPC is an essential component of network applications. IPC enables different processes to communicate and coordinate their activities which is necessary for the proper functioning of the application.
The Interface Between the Process and the Computer Network
Most applications, as previously stated, are made up of pairs of communicating processes, with the two processes in each pair sending messages to each other. Any message sent from one process to another must traverse the underlying network.
Sending data across a network is a complex operation that must be carefully tuned to the network’s physical characteristics as well as the logical nature of the data being sent. Software that sends data across a network must know how to avoid packet collisions, convert digital data to analog signals, detect and correct errors, route packets from one host to another, and more. When the requirement to support multiple operating systems and heterogeneous network cabling is added, the process becomes even more complicated.
The various aspects of network communication are separated into multiple layers to hide the majority of this complexity from the application developer and end user. Each layer denotes a different level of abstraction between the physical hardware (wires and electricity) and the data being transmitted. In theory, each layer only communicates with the layers immediately above and below it. The ability to separate the network into layers allows you to modify or even replace software in one layer without affecting the others, as long as the interfaces between the layers remain the same.
While the middle layer protocols are fairly consistent across the majority of the Internet today, the top and bottom layers vary significantly. Some hosts use Ethernet, while others use WiFi, PPP, or something else. Similarly, what’s at the top of the stack is entirely dependent on the programs that a host is running. The key point is that what’s at the bottom doesn’t really matter from the top, and vice versa. The layer model decouples application protocols (the primary focus of this course) from the physics of network hardware and network topology.
There are several different layer models, each organized to meet the needs of a specific type of network. The below figure depicts the standard TCP/IP four-layer Internet model used in this course.
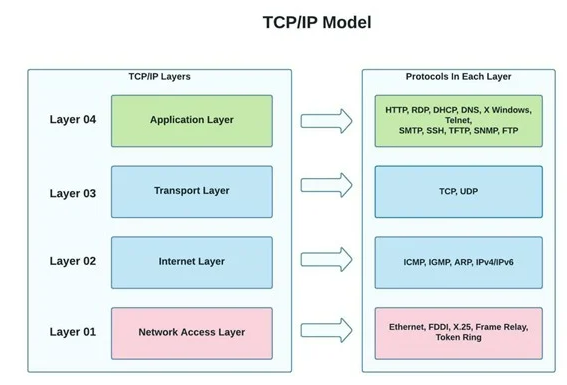
Applications such as Firefox and Warcraft run in the Application Layer and communicate only with the Transport Layer in this model. The Transport Layer only communicates with the Application Layer and the Internet Layer.
The Internet Layer, in turn, communicates only with the Network Access Layer the Transport Layer, but never with the Application Layer directly. Network Access Layer is also known as Host-to-Network Layer. The Host-to-Network Layer sends data across wires, fiber-optic cables, or other medium to the remote system’s Host-to-Network layer, which then sends data up the layers to the remote system’s application.
However, 90% of the time, your Java code will operate in the Application Layer and will only require communication with the Transport layer. The other 10% of the time, you’ll be in the Transport Layer, communicating with the Application Layer or the Internet Layer. The point of the layer model is to hide the complexity of the host-to-network layer from you.
The network creates a logical path between the two Application Layers, giving the Application Layer the impression that it is communicating directly with the Application Layer on the other system. Consider an Messenger chat session to help you understand the logical path. Most people in a Messenger chat would say they’re talking to someone else. If you press them too hard, they may claim to be talking to their computer (really the Application Layer), which is talking to the other person’s computer, which is talking to the other person. Everything deeper than one layer is effectively invisible, which is exactly how it should be.
Let us briefly discuss the four layers to understand why interfaces are needed for communication between two processes.
Host-to-Network
As a Java programmer, you are near the top of the network food chain. A lot goes on behind the scenes. The Host-to-Network Layer (also known as the Link Layer, Data Link Layer, or Network Interface Layer) is responsible for the network’s hidden parts in the standard reference model for IP-based Internets (the only type of network Java truly understands) . The Host-to-Network Layer specifies how a network interface, such as an Ethernet card or a WiFi antenna, sends IP datagrams over its physical connection to the local network and the rest of the world.
You don’t need to worry about this layer as a Java programmer unless something goes wrong—the plug falls out of the back of your computer, or someone drops a backhoe through the T-1 line that connects you to the rest of the world. In other words, Java never comes into contact with the physical layer.
Internet Layer
The Internet Layer is the next layer of the network and the first one with which you should be concerned. The Internet Layer is known as the Network Layer in the OSI model. A Network Layer protocol specifies how bits and bytes of data are organized into larger groups known as packets, as well as the addressing scheme used to connect machines. The Internet Protocol (IP) is the most widely used Network Layer protocol on the planet, and it is the only one that Java understands.
Aside from routing and addressing, the Internet Layer’s second purpose is to allow different types of Host-to-Network Layers to communicate with one another. Internet routers convert WiFi to Ethernet, Ethernet to DSL, DSL to fiber-optic backhaul protocols, and so on. Without the Internet Layer or something similar, each computer could only communicate with other computers on the same network. The Internet Layer is in charge of connecting heterogeneous networks using homogeneous protocols.
The Transport Layer
Raw packets have some disadvantages. Most importantly, there is no assurance that they will be delivered. Even if they are delivered, they may have been tainted during transportation. The header checksum can only detect corruption in the header and cannot detect corruption in the data portion of a datagram. Finally, even if the packets arrive intact, they may not arrive in the order in which they were sent. Individual packets may take various paths from source to destination. The fact that packet A is sent before packet B does not guarantee that packet A will arrive before packet B.
The Transport Layer is in charge of ensuring that packets arrive in the order in which they were sent and that no data is lost or corrupted. If a packet is lost, the Transport Layer can request that the sender resend the packet. IP networks accomplish this by appending a new header to each datagram that contains additional information. At this level, there are two primary protocols.
The Transmission Control Protocol (TCP) is a high-overhead protocol that allows for the retransmission of lost or corrupted data as well as the delivery of bytes in the order they were sent.
The User Datagram Protocol (UDP), the second protocol, allows the receiver to detect corrupted packets but does not guarantee that packets are delivered in the correct order (or at all). However UDP is much faster than TCP. TCP is known as a reliable protocol, whereas UDP is known as an unreliable protocol. You’ll see later that untrustworthy protocols are far more useful than they appear.
The Application Layer
The Application Layer is the layer that delivers data to the user. The three lower layers all collaborate to define how data is transferred from one computer to the next. After the data is transferred, the Application Layer determines what to do with it. For example, an Application Layer Protocol such as HTTP (for the World Wide Web) ensures that a graphic image is displayed as a picture rather than a long stream of numbers by your web browser.
The Application Layer is where the majority of your programs’ network components spend their time. In addition to HTTP for the Web, there are SMTP, POP, and IMAP for email; FTP, FSP, and TFTP for file transfer; NFS for file access; Gnutella and BitTorrent for file sharing; the Session Initiation Protocol (SIP) and Skype for voice communication; and many, many more. Your programs can also define their own application layer protocols as needed.
We need some mechanism to send data from one layer to another so that it can reach from one host to another. This mechanism is provided by the network interface.
In the next tutorial we will talk a lot about network interfaces.



